By: Karrie Westmoreland
In the ever-evolving theater of cyber warfare, threat actors have found a new canvas for their exploits — your family photos, your favorite memes, and even corporate marketing images. Welcome to the world of steganography-powered cyberattacks, where malware doesn’t knock on the door — it sneaks in, pixel by pixel.
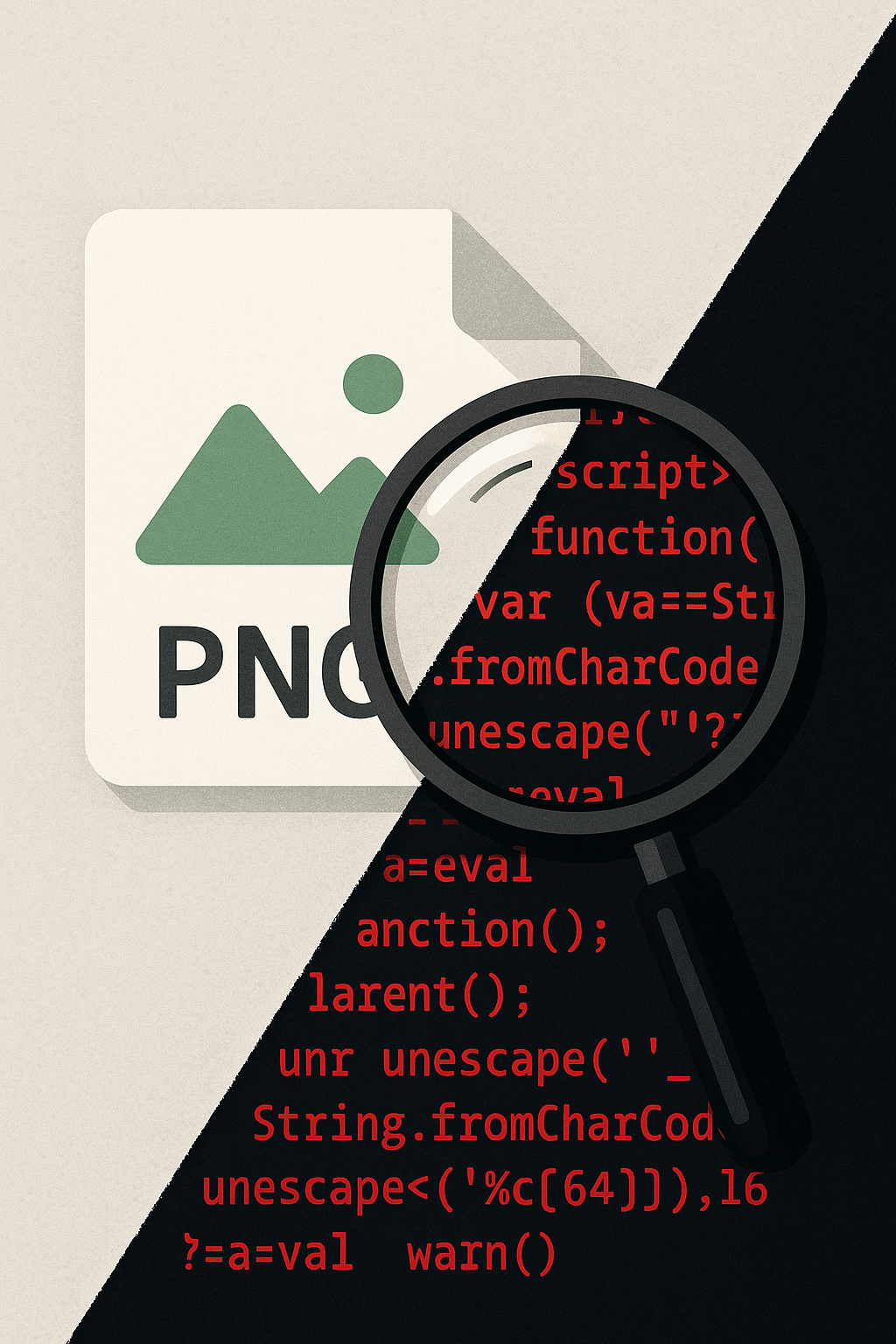
At its core, steganography is the ancient art of hiding information in plain sight. Unlike encryption, which scrambles data into unreadable gibberish, steganography conceals the existence of the data altogether. To the naked eye (and often to traditional security scanners), a stego-laden image looks perfectly normal.
- Malware is embedded into an image file — JPEG, PNG, even GIFs — without noticeably altering the visual output.
- The image is attached to an email, often under the guise of an invoice, an invitation, or a marketing promotion.
- Once the unsuspecting recipient downloads or previews the image, hidden payloads are extracted via specially crafted scripts or vulnerabilities.
Think of it as a trojan horse, only a lot more pixelated.
Here's how cybercriminals typically use this clever subterfuge:
- Image Preparation: Attackers embed malicious code into an image file using tools like Steghide, OpenStego, or customized scripts. This code might be a dropper, a remote access trojan (RAT), or commands for an already-compromised system.
- Social Engineering Bait: Leveraging urgent themes — like “Unpaid Invoice Attached” or “Urgent Staff Update!” — the attacker sends an email with the weaponized image attached or linked.
- Initial Execution: The email may contain macros, HTML smuggling techniques, or rely on user actions (like downloading and opening the image). Once opened, hidden malware is extracted and executed, often bypassing basic security defenses that only scan visible file content.
- Payload Delivery: The payload could exfiltrate sensitive information, open backdoors, or deploy ransomware. In sophisticated campaigns, the images act as command-and-control (C2) beacons, pulling in instructions from hidden messages.
- Operation Stegoloader (2015): Discovered in 2015, this campaign involved malware that downloaded additional malicious components by hiding them inside PNG image files. Targeting healthcare, education, and manufacturing sectors, Stegoloader was particularly notable for its stealthy operations designed to evade endpoint detection.
- OilRig Group Tactics: The Iran-linked APT group has used steganography to hide C2 communications inside innocent-looking image files, effectively bypassing network-based detection systems.
- LuckyMouse Campaign: This sophisticated actor leveraged BMP images to embed shellcode, using email-based spear-phishing campaigns primarily aimed at government and defense organizations.
In every case, the payloads hid in plain sight, sailing right past many organizations' traditional endpoint security and email filtering solutions.
- Human Trust in Images: Most users (and even some security protocols) consider images “safe” compared to executable files.
- Email Filters' Blind Spots: Many email security tools prioritize attachments like ZIPs, DOCXs, and EXEs for inspection — images often receive less scrutiny.
- Bypassing Sandboxing: Sandboxes typically look for "suspicious behavior" — opening a harmless-looking JPEG file doesn’t immediately set off alarm bells.
In essence, steganography weaponizes our trust and assumptions about innocuous digital content.
- Content Disarm and Reconstruction (CDR): Strip and rebuild file attachments, neutralizing hidden code without affecting visible content. Products like Votiro and Glasswall specialize in this method.
- Advanced Email Security: Deploy email gateways capable of deep content inspection beyond surface-level metadata. Solutions from Proofpoint, Mimecast, and Microsoft Defender for Office 365 now offer enhanced image scanning options.
- Network Anomaly Detection: Use AI-powered tools to detect unusual outbound traffic, like hidden C2 communications disguised as image downloads.
- Employee Training: Conduct awareness sessions on recognizing suspicious attachments — yes, even “harmless” image files. Promote a “trust, but verify” approach to all unexpected communications.
- Zero Trust Architecture: Assume no file, no email, no source is automatically trustworthy. Apply strict policies around file downloads, even from "known" senders.
- Unexpected invoices or promotions with generic greetings ("Dear Customer").
- Pressure to download an image urgently.
- Poor grammar or slightly 'off' branding.
- Image files with weird double extensions (e.g., invoice.jpg.exe).
Golden Rule: If you didn’t ask for it, don’t download it — even if it looks like a simple image.
- Don’t open attachments from unknown senders.
- Hover over links before clicking; verify senders independently.
- Report suspicious emails immediately to IT/security teams.
- When in doubt, delete the email without opening it.
Threat actors are constantly looking for new ways to slip past our defenses, and steganography offers a dangerously effective method to do so. As cyber defenders, we must not just see — we must see through. The next time you receive a cute puppy photo from an unknown sender, remember: behind those adorable eyes could lurk the cold, calculating gaze of a hidden threat.
Stay alert. Stay skeptical. And never underestimate the power of a pixel.
Subscribe To Our Newsletter
Get updates and learn from the best
More To Explore